A firewall is a network security device whose main function is to monitor and control network traffic entering and exiting a network through a set of rules. It can determine which traffic is allowed to pass and which needs to be blocked based on a predefined set of security rules. A firewall can be a hardware device, a software program, or a combination of both. Its primary purpose is to protect the network from unauthorized access and potential security threats. It filters data packets through rule settings, blocking suspicious activities and malicious traffic from entering the internal network. The functions of a firewall are not limited to simple packet filtering; they can also include more complex intrusion detection systems (IDS) and intrusion prevention systems (IPS).
The history of firewalls dates back to the 1980s. With the popularization of the Internet and the increase in network threats, firewall technology has also continuously developed. Early firewalls mainly relied on static packet filtering, while modern firewalls combine multiple security technologies such as deep packet inspection (DPI), application layer gateways (ALG), and next-generation firewalls (NGFW). Currently, firewalls have become a key component of network security, playing an important role in protecting enterprise and personal network security.

Functions and Roles of Firewalls
1. Traffic Filtering Basics
- **Packet filtering based on IP address, port, and protocol**: Firewalls inspect incoming and outgoing network data packets according to predefined rules. It can decide whether to allow a data packet to pass based on information such as source address, destination address, source port, destination port, and protocol type (e.g., TCP, UDP, ICMP). This basic filtering method ensures that only data packets that meet specific criteria can enter or leave the network.
- **Stateful Packet Inspection (SPI)**: Stateful inspection firewalls not only check the header information of data packets but also monitor the state of the data packets. SPI firewalls can identify and track the state of each connection, such as the establishment, progress, and closure of the connection, thereby only allowing data packets related to existing connections to pass and blocking unauthorized connection attempts.
- **Application layer filtering**: Some advanced firewalls can filter at the application layer (Layer 7 of the OSI model) and analyze the content and context of data packets. This filtering method can identify and block traffic from specific applications or services, such as prohibiting the transmission of certain file types or blocking the operation of specific applications.
2. Intrusion Prevention
- **Intrusion Detection System (IDS)**: Firewalls can integrate an intrusion detection system, which identifies potential intrusion behaviors by monitoring network traffic and system activities. IDS can detect abnormal behaviors, suspicious traffic, and known attack patterns, and issue alerts to administrators for timely measures.
- **Intrusion Prevention System (IPS)**: Compared with IDS, the Intrusion Prevention System (IPS) is more proactive. It can not only detect attacks but also automatically take actions to block them. IPS can intercept and block malicious traffic in real-time to ensure network security.
3. Privacy Protection
- **NAT (Network Address Translation) function**: Firewalls usually have a NAT function, which can convert private IP addresses of the internal network into public IP addresses, thereby hiding the internal network structure and increasing security. NAT can also effectively save IP address resources, allowing multiple devices to share a public IP address to access the Internet.
- **VPN support**: Firewalls usually support Virtual Private Network (VPN) functions, allowing remote users to securely access the internal network through encrypted tunnels. VPN ensures the confidentiality and integrity of data during transmission, effectively preventing data leakage and tampering.
4. Logging and Auditing
- **Recording traffic logs**: Firewalls can record detailed network traffic logs, including source, destination, port, protocol, and time. These logs provide important reference for administrators, facilitating network traffic analysis, troubleshooting, and security auditing.
- **Generating security reports**: Firewalls can regularly generate security reports, summarizing network activities and security incidents. Reports can help administrators understand the network security status, identify potential security risks, and adjust security policies in a timely manner.
Types of Firewalls
1. Hardware Firewalls
- **Dedicated devices**: Hardware firewalls are specially designed devices with independent hardware resources such as CPU, memory, and storage, used to efficiently process network traffic and security functions. They are usually installed at the network boundary to protect the internal network from external threats.
- **High performance and stability**: Due to their dedicated hardware design, hardware firewalls can handle a large number of concurrent connections and high traffic, providing high performance and stability. They are suitable for environments that require high security and performance, such as large enterprises and data centers.
2. Software Firewalls
- **Software installed on servers or PCs**: Software firewalls are software that can be installed on operating systems to monitor and control network traffic entering and exiting devices. Common ones include Windows Firewall, iptables (Linux), and firewall functions integrated with antivirus software.
- **Flexible configuration**: Software firewalls are highly flexible, and users can customize security policies and rules as needed. They are suitable for small and medium-sized enterprises, individual users, and environments that require flexible configuration.
3. Next-Generation Firewalls (NGFW)
- **Combining traditional firewalls with advanced security functions**: Next-Generation Firewalls (NGFW) combine the packet filtering functions of traditional firewalls with modern security technologies such as deep packet inspection (DPI), intrusion prevention systems (IPS), application identification and control, etc.
- **Deep packet inspection and application identification**: NGFW can deeply inspect the content of data packets, identify application layer protocols and applications, and finely control and protect network traffic. They provide higher security and can defend against complex network attacks.
4. Cloud Firewalls
- **Cloud-based firewall services**: Cloud firewalls are firewall services deployed and managed in cloud environments, usually provided by cloud service providers (such as AWS, Azure, Google Cloud). They protect cloud resources and applications from network threats.
- **Suitable for cloud computing environments**: Cloud firewalls are flexible and scalable, suitable for dynamically changing cloud computing environments. They can provide consistent security policies and protection across multiple cloud regions and data centers.
Working Principles of Firewalls
1. Packet Filtering
- **Checking the source address, destination address, port, and protocol of each data packet**: Firewalls inspect each incoming and outgoing data packet according to a predefined rule set. It can decide whether to allow the data packet to pass based on information such as the source address, destination address, source port, destination port, and protocol type (e.g., TCP, UDP, ICMP) of the data packet.
- **Deciding to allow or block based on rules**: If a data packet meets the conditions in the security rule set, the firewall will allow it to pass; otherwise, the data packet will be blocked. This packet filtering method ensures that only data packets that meet specific security conditions can enter or leave the network.
2. State Inspection
- **Monitoring the state of connections**: Stateful inspection firewalls (SPI) not only check the header information of data packets but also monitor the state of each connection. SPI firewalls can identify and track the state of each connection, including the establishment, progress, and closure of the connection.
- **Allowing data packets of legitimate connections to pass and blocking those of illegal connections**: SPI firewalls only allow data packets related to existing connections to pass and block unauthorized connection attempts, ensuring the legality and security of network connections.
3. Proxy Service
- **Acting as an intermediary to proxy network requests**: Firewalls can act as proxy servers, sending requests to external networks on behalf of devices in the internal network and returning responses from external networks to internal devices. Proxy services enhance security by hiding the structure of the internal network.
- **Hiding the internal network structure to enhance security**: Proxy services prevent external networks from directly accessing internal devices, reducing the attack surface and enhancing network security and privacy protection.
4. Deep Packet Inspection
- **Inspecting the content of data packets**: Deep Packet Inspection (DPI) technology allows firewalls to deeply inspect the content of data packets, not just the header information. DPI can analyze the payload part of data packets to identify application layer protocols and content.
- **Detecting and blocking malware and attacks**: Through DPI, firewalls can identify and block malicious content such as malware, viruses, worms, and Trojan horses, as well as complex network attacks such as SQL injection and cross-site scripting (XSS).
Application Scenarios of Firewalls
1. **Enterprise network security**: In an enterprise environment, firewalls are used to protect the internal network from attacks from external networks (such as the Internet). Firewalls can block unauthorized access while allowing legitimate communications to pass.
2. **Data centers**: Data centers store a large amount of sensitive information, such as user data and financial information. The role of firewalls here is to prevent data leakage and unauthorized access.
3. **Personal device protection**: Firewalls can also be installed on personal devices (such as computers and mobile phones) to prevent malware intrusion and leakage of personal information.
4. **Internet of Things (IoT) security**: With the popularization of IoT devices, such as smart home devices and industrial control systems, the application of firewalls on these devices is becoming more and more widespread. Firewalls can prevent these devices from being hacked and protect their normal operation.
5. **Virtual Private Network (VPN)**: Firewalls are often used together with Virtual Private Networks (VPNs). VPN can create a secure network connection, and firewalls can protect this connection from attacks.
Router
Router
A router is a device that connects multiple networks and is responsible for transmitting data packets between these networks. It selects the best path based on the destination IP address and transmits data packets from one network to another.
The main function of a router is routing at the network layer. It uses routing tables and routing protocols to determine the best transmission path for data packets. By checking the target IP address of each data packet and based on the content of the routing table, the router decides which next-hop router or final destination device to send the data packet to. Routers are widely used in both home and enterprise networks, helping users connect to the Internet and transmit data between local area networks (LANs) and wide area networks (WANs).
In addition to basic routing functions, modern routers also provide a variety of additional functions, such as firewall functions, VPN support, QoS (Quality of Service) management, and NAT (Network Address Translation). These additional functions enable routers not only to forward data packets but also to enhance network security, manageability, and performance.
Routers are at the core of the network architecture. Home routers are usually used to connect home devices to Internet Service Providers (ISPs), while enterprise-level routers are used to manage more complex network environments, supporting a large number of devices and high traffic demands.

Functions and Roles of Routers
1. Routing
- **Static routing and dynamic routing**: Routers can select transmission paths for data packets through static routing and dynamic routing. Static routing is a fixed routing path manually configured by administrators, while dynamic routing automatically learns and updates through routing protocols. Dynamic routing can automatically adjust routing paths according to changes in the network topology, improving network flexibility and fault tolerance.
- **Supporting multiple routing protocols**: Routers support multiple routing protocols, such as RIP (Routing Information Protocol), OSPF (Open Shortest Path First), and BGP (Border Gateway Protocol). These protocols help routers effectively select the best path in large and complex networks, ensuring that data packets can be transmitted efficiently and reliably.
2. Connection Management
- **Connection between LAN and WAN**: Routers can connect different Local Area Networks (LANs) and Wide Area Networks (WANs) to realize data transmission between networks. It can connect home or enterprise internal networks to the network of Internet Service Providers (ISPs) to achieve Internet access.
- **VPN support**: Routers usually support VPN functions, allowing users in different locations to securely access the internal network through encrypted tunnels. VPN connections not only improve the security of data transmission but also make communication between remote offices and branches more convenient.
3. Network Segmentation
- **Subnet division and VLAN support**: Routers can divide a large network into multiple subnets, reasonably allocate IP addresses and network resources, and improve network manageability and security. In addition, routers also support VLAN (Virtual Local Area Network) functions, which further isolate network traffic through logical network division and enhance network security and performance.
4. Network Optimization
- **QoS management**: Routers support QoS (Quality of Service) management, which ensures that key applications and services receive sufficient bandwidth and priority processing through means such as priority division and bandwidth allocation, improving the overall performance of the network and user experience.
- **Bandwidth management**: Routers can monitor and control the use of network bandwidth, preventing individual users or applications from occupying excessive bandwidth, and ensuring the rational allocation and efficient use of network resources.
Types of Routers
1. Home Routers
- **Providing home network connections**: Home routers are designed for small home networks, providing basic routing functions to connect home devices (such as computers, mobile phones, smart home devices) to Internet Service Providers (ISPs).
- **Integrating wireless functions**: Most home routers integrate wireless access points (Wi-Fi) to support wireless device connections and provide convenient home wireless networks.
2. Enterprise-Level Routers
- **High performance and multiple functions**: Enterprise-level routers are designed for medium and large enterprise networks, with high performance and rich functions, such as advanced routing protocols, redundant design, and multi-WAN port support.
- **Supporting a large number of devices and complex network configurations**: These routers can support a large number of concurrent connections, handle complex network topologies and configurations, and ensure the reliability and security of enterprise networks.
3. Edge Routers
- **Connecting enterprise networks and ISPs**: Edge routers are deployed at the boundary of enterprise networks, connecting enterprise internal networks with the networks of Internet Service Providers (ISPs), and managing traffic entering and exiting the network.
- **Handling high traffic and security requirements**: Edge routers usually need to handle high traffic, provide advanced security functions (such as VPN, DDoS protection), and support Quality of Service (QoS) management to ensure the security and performance of the network boundary.
4. Core Routers
- **Backbone devices of large networks**: Core routers are deployed at the core of large networks as network backbone devices, connecting multiple branch routers and switches, and providing high-speed and reliable data transmission.
- **High throughput and reliability**: Core routers need to handle a large amount of data traffic, with high throughput, high availability, and redundant design to ensure network continuity and stability.
Working Principles of Routers
1. Routing
- **Determining the transmission path of data packets according to the routing table**: Routers use routing tables to determine the transmission path of data packets. The routing table contains the addresses of target networks and information about the next-hop routers to reach these networks. By looking up the routing table, the router determines the best transmission path for data packets.
- **Dynamically updating the routing table using routing protocols**: Routers automatically learn and update routing tables by running routing protocols (such as RIP, OSPF, BGP). Routing protocols help routers adapt to changes in the network topology, ensuring that data packets can find the best path for transmission.
2. Data Packet Forwarding
- **Checking the target IP address**: When a data packet arrives at the router, the router checks the target IP address of the data packet and looks up the routing table based on the target IP address to decide which interface to send the data packet to.
- **Forwarding data packets**: According to the results of the routing table, the router forwards the data packet to the corresponding interface for transmission to the next router or the final destination device. This process ensures that data packets can be transmitted from the source address to the target address along the optimal path.
3. NAT (Network Address Translation)
- **Converting IP addresses**: Network Address Translation (NAT) is a technology that realizes data packet forwarding by modifying IP address information. Routers use NAT to convert private IP addresses of the internal network into public IP addresses, enabling internal devices to share a public IP address to access the Internet.
- **Hiding the internal network structure**: NAT can also hide the structure of the internal network and increase network security. External networks can only see public IP addresses and cannot directly access internal devices.
4. Firewall Function
- **Basic firewall rules**: Some routers integrate basic firewall functions, which can filter and control data packets according to predefined rules to protect the network from unauthorized access and attacks.
- **Advanced security functions**: Advanced routers may have more security functions, such as intrusion detection and prevention, content filtering, and VPN support, providing comprehensive network security protection.
Application Scenarios of Routers
1. **Home networks**: In a home environment, routers are usually used to connect multiple devices in the home, such as computers, mobile phones, and smart TVs, and provide Internet access.
2. **Enterprise networks**: In an enterprise environment, routers are used to connect the enterprise‘s internal network and external networks (such as the Internet), and can implement complex network strategies such as load balancing and VPN.
3. **Data centers**: In data centers, routers are used to connect a large number of servers and provide high-speed and high-reliability network connections.
4. **Internet Service Providers (ISPs)**: Internet Service Providers (ISPs) use routers to manage and control a large amount of user traffic and provide Internet access services.
5. **Internet of Things (IoT)**: In IoT environments, routers can connect various IoT devices, such as smart home devices and industrial control systems, and provide Internet connections.
Switch

A switch is a network device used to connect multiple devices in a Local Area Network (LAN). Switches realize communication between devices by exchanging data frames. Working at the data link layer, switches forward data frames through MAC address tables.
The main function of a switch is to forward and filter data frames. It can determine the transmission path of data according to the MAC address of the data frame. Switches usually have multiple ports and can connect multiple computers, printers, servers, and other devices to form a local area network.
Switches are widely used in both enterprise and home networks, providing efficient LAN connections and data transmission. By learning and recording the MAC addresses of each connected device, switches establish and maintain MAC address tables, and then forward data frames to the corresponding ports according to the target MAC address. This MAC address-based forwarding mechanism enables switches to efficiently handle network traffic, reduce conflicts and congestion, and improve network performance.
Switches are usually divided into unmanaged switches and managed switches. Unmanaged switches provide basic connection functions and are suitable for small networks and home networks, while managed switches provide advanced management and configuration functions, such as VLAN (Virtual Local Area Network) support, QoS (Quality of Service) management, traffic monitoring and control, etc., and are suitable for large and complex enterprise network environments.

Functions and Roles of Switches
1. Data Frame Forwarding
- **Frame forwarding based on MAC address**: Switches build MAC address tables by learning and recording the MAC addresses of each connected device. It forwards data frames to the corresponding ports according to the target MAC address of the data frame. This MAC address-based forwarding mechanism enables switches to efficiently handle network traffic, reducing conflicts and congestion.
- **Full-duplex communication**: Modern switches usually support full-duplex communication, allowing devices to send and receive data at the same time, improving network throughput and communication efficiency.
2. Network Expansion
- **Providing multiple ports for network expansion**: Switches usually have multiple ports and can connect multiple computers, printers, servers, and other devices to form a Local Area Network (LAN). By connecting multiple switches, the network scale can be further expanded and the number of device connections can be increased.
- **Supporting stacking and link aggregation**: Some advanced switches support stacking and link aggregation functions. Stacking allows multiple switches to be managed and operated as a logical switch, improving network scalability and manageability. Link aggregation binds multiple physical links together to provide higher bandwidth and redundancy.
3. VLAN Support
- **Virtual Local Area Network division**: Switches support VLAN (Virtual Local Area Network) functions, which isolate network traffic of different departments or users through logical network division. VLAN not only improves network security but also enhances network manageability and flexibility.
- **Enhancing network security and management**: Through VLAN division, switches can effectively prevent broadcast storms and network congestion, improving network stability and security. In addition, VLAN makes network management more flexible and convenient, and administrators can adjust network structure and access permissions as needed.
4. Traffic Management
- **Traffic monitoring and control**: Switches can monitor network traffic, detect and control abnormal traffic, and prevent network congestion and performance degradation. Traffic control functions ensure the rational use of network resources and improve the overall performance of the network.
- **Supporting QoS management**: Switches usually support QoS (Quality of Service) management, which ensures that key applications and services receive sufficient bandwidth and priority processing through means such as priority division and bandwidth allocation, improving the overall performance of the network and user experience.
Types of Switches
1. Unmanaged Switches
- **Simple and easy to use**: Unmanaged switches are simply designed, can be used by plugging in the power and network cables, and do not require configuration and management, suitable for small offices or home networks.
- **Basic connection functions**: Provide basic network connection functions, suitable for simple network environments, and cannot perform advanced functions such as VLAN division and QoS management.
2. Managed Switches
- **Providing advanced management and configuration functions**: Managed switches support configuration and management through command-line interface (CLI), graphical user interface (GUI), or network management protocols (such as SNMP), and provide advanced functions such as VLAN, QoS, link aggregation, and traffic monitoring.
- **Suitable for large and complex networks**: These switches are suitable for enterprise networks and data centers that require fine control and management, providing high performance and flexible network management capabilities.
3. Smart Switches
- **Between unmanaged and managed switches**: Smart switches provide partial management functions, more powerful than unmanaged switches, but not as complex as fully managed switches. They are suitable for small and medium-sized enterprises that need some advanced functions but not comprehensive management.
- **Providing VLAN and basic QoS functions**: Support VLAN division, basic QoS management, and provide a certain degree of traffic control and network optimization.
4. Stackable Switches
- **Multiple switches stacked into one logical device**: Stackable switches stack multiple physical switches into one logical switch through dedicated stacking interfaces and cables, which are managed and configured uniformly.
- **Improving scalability and manageability**: Stackable switches are suitable for large enterprise networks that require high scalability and simplified management. Network expansion is achieved through stacking, providing redundancy and high availability.
Working Principles of Switches
1. MAC Address Learning
- **Recording the MAC addresses of connected devices**: By receiving data frames, switches record the MAC addresses of devices connected to each port and store them in the MAC address table. Each time a device sends a data frame, the switch updates the MAC address table to ensure that the information in the table is up-to-date.
- **Dynamically updating the MAC address table**: Switches can dynamically learn and update MAC address tables. When a new device is connected to the switch, the switch automatically records the device‘s MAC address and connection port, maintaining the accuracy of the MAC address table.
2. Data Frame Forwarding
- **Looking up the target MAC address**: When a switch receives a data frame, it checks the target MAC address of the data frame and looks for the corresponding port in the MAC address table.
- **Forwarding data frames**: According to the results of the MAC address table, the switch forwards the data frame to the corresponding port to transmit data to the target device. This MAC address-based forwarding mechanism ensures that data frames can be efficiently transmitted to the correct device.
3. Broadcast and Multicast Processing
- **Processing broadcast data frames**: When a switch receives a data frame with the target MAC address as the broadcast address, it copies and sends the data frame to all ports to ensure that all devices in the network can receive the data frame.
- **Processing multicast data frames**: Switches support the processing of multicast data frames, which can forward data frames to specific port groups according to multicast group addresses, reducing unnecessary network traffic and improving network efficiency.
4. VLAN (Virtual Local Area Network)
- **Logically dividing the network**: Through VLAN functions, switches can divide physical networks into multiple logical subnets. Each VLAN serves as an independent broadcast domain, isolating network traffic of different departments or users.
- **Enhancing network security and performance**: VLAN can effectively prevent broadcast storms and network congestion, improving network security and performance. Administrators can configure and manage VLANs as needed to achieve flexible network management and optimization.
Application Scenarios of Switches
1. **Enterprise networks**: In an enterprise environment, switches are used to connect internal network devices of the enterprise, such as computers, printers, and servers, and provide high-speed network connections.
2. **Data centers**: In data centers, switches are used to connect a large number of servers and provide high-speed and high-reliability network connections. Switches can also implement complex network strategies such as load balancing and VLAN.
3. **Home networks**: In a home environment, switches are usually used to expand the connection capability of home networks, such as connecting multiple computers, smart TVs, and other devices.
4. **Schools and universities**: In school and university environments, switches are used to connect network devices in classrooms, laboratories, libraries, etc., and provide Internet access.
5. **Internet Service Providers (ISPs)**: Internet Service Providers (ISPs) use switches to manage and control a large amount of user traffic and provide Internet access services.
Firewall vs Router vs Switch
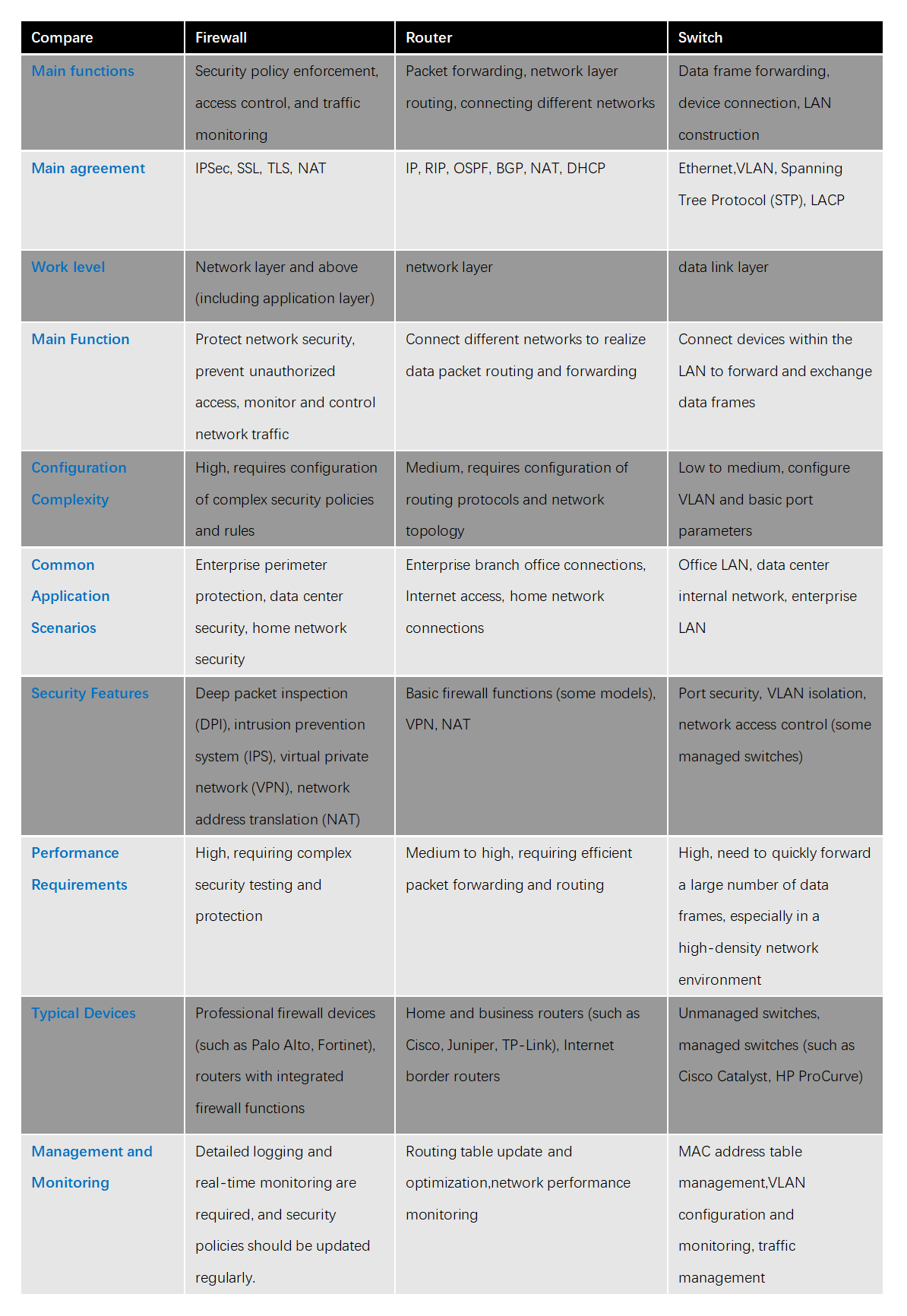
Firewall vs Router vs Switch



















 Teamas
Teamas